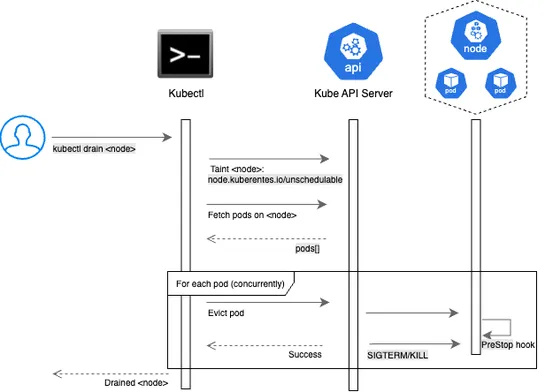
Rethinking Node Drains: A Webhook Based Approach to Graceful Pod Removal
Eviction Reschedule Hooksticks its nose in Kubernetes eviction requests, letting operator-managed stateful apps wriggle their way through node drains without breaking a sweat. 🎯.. read more