Top 7 Observability Platforms That Auto-Discover Services
Auto-discovery tools now detect services as they appear and build dashboards instantly. Here are seven platforms that do it well.
Join us
Auto-discovery tools now detect services as they appear and build dashboards instantly. Here are seven platforms that do it well.

Hey, sign up or sign in to add a reaction to my post.
Pro tips to write dockerfiles. Cut your build timing of your images by half.

Hey, sign up or sign in to add a reaction to my post.
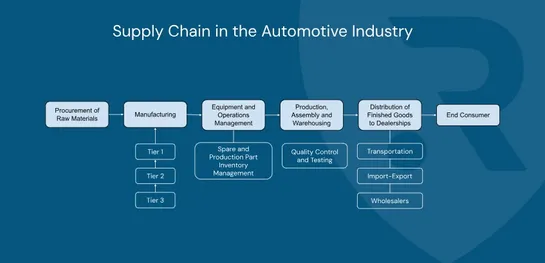
The major cyberattack that halted Jaguar Land Rover’s production for almost six weeks has exposed a hard truth: modern automotive manufacturing is deeply vulnerable to digital disruption. From frozen assembly lines to supplier chaos and regional economic fallout, the incident showed how quickly a si..
Hey, sign up or sign in to add a reaction to my post.
Understand how AWS Fargate runs your ECS containers without servers—just define CPU, memory, and networking, and AWS handles the compute.

Hey, sign up or sign in to add a reaction to my post.
Helm v4 has been released a week ago. Its highlights are: - Server-Side Apply instead of 3-Way Merge - WASM plugins - Using kstatus for resource tracking - Content-based chart caching This articleprovides a detailed overview of why these changes were made in Helm v4 and what they bring for Helm user..
Hey, sign up or sign in to add a reaction to my post.
Today we highlight our main diagram “Airport Software Systems”, showcasing how integrated airport management platforms —from AODB to landside & airside operations, billing, and information systems— work together to ensure efficient and secure airport operations. We also explain how load balancing en..

Hey, sign up or sign in to add a reaction to my post.
OTLP 1.9.0 adds support for maps, arrays, and byte arrays across all OTel signals. Here's when to use complex attributes and when to stick with flat.

Hey, sign up or sign in to add a reaction to my post.
📢 At RELIANOID, we follow SOC 2 Trust Service Criteria to ensure Security, Availability, Confidentiality, Processing Integrity, and Privacy across our load balancing solutions — whether on-prem, cloud, or hybrid. Our controls align with the needs of highly regulated environments such as finance, hea..
Hey, sign up or sign in to add a reaction to my post.
Chinese state-backed threat actorsorchestrated automated cyber attacks using AI technology developed byAnthropicin a highly refinedespionage campaignin mid-September 2025. The attackers leveraged AI to execute 80-90% of tactical operations independently at physically impossible request rates, markin.. read more

Hey, sign up or sign in to add a reaction to my post.
TheModel Context Protocol (MCP)wires AI agents into real-world dev workflows, think pushing to GitHub, deploying APIs, tweaking Docker, all straight from the code editor. MCP servers like GitHub MCP, Apidog MCP, and Supabase MCP plug into popular tools and infra. They let LLMs update code, ship APIs.. read more

Hey, sign up or sign in to add a reaction to my post.
This tool doesn't have a detailed description yet. If you are the administrator of this tool, please claim this page and edit it.
Hey there! 👋
I created FAUN.dev(), an effortless, straightforward way to stay updated with what's happening in the tech world.
We sift through mountains of blogs, tutorials, news, videos, and tools to bring you only the cream of the crop — so you can kick back and enjoy the best!
