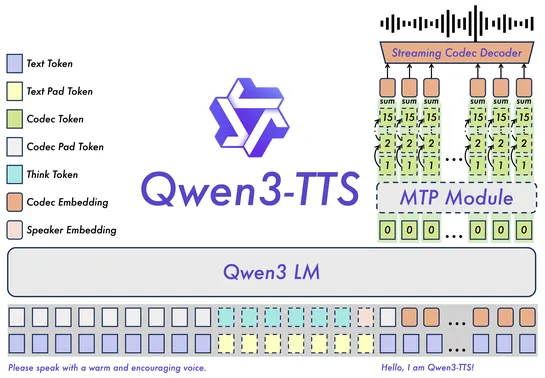
How we built an AI SRE agent that investigates like a team of engineers
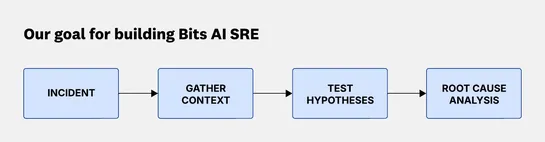
Datadog just droppedBits AI SRE, an autonomous agent that thinks more like an SRE than a chatbot. It doesn't just regurgitate summaries - it investigates. It builds hypotheses, tests them against telemetry, and chases down actual root causes. Older tools leaned hard on LLMs to summarize alerts. That.. read more