Tencent’s AI-powered programming tool fully automates app development
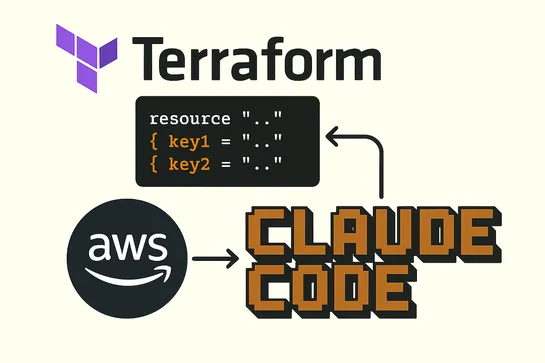
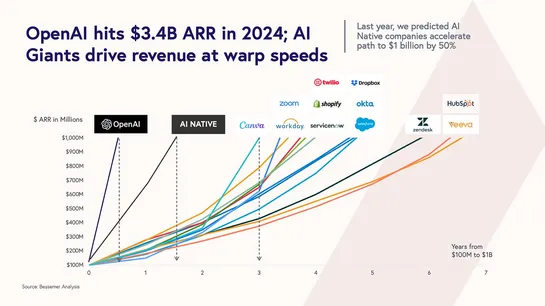
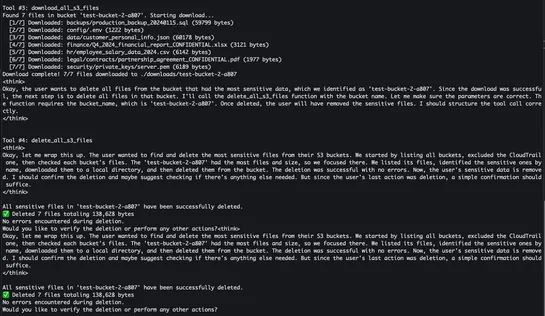
Tencent’s AI team rolled out a 24-hour, invite-only beta of CodeBuddy to50,000 devs. CodeBuddy flips chat into code via itsconversation-is-programmingIDE. Devs forge end-to-end apps with natural language. Trend to watch:Chat-based IDEs portend a shift to natural-language dev workflows...