Thousands of Software Engineers Say the Job Market Is Getting Much Worse
9,388 engineers polled by Motherboard and Blind said AI will lead to less hiring. Only 6% were confident they'd get another job with the same pay... read more
Join us
9,388 engineers polled by Motherboard and Blind said AI will lead to less hiring. Only 6% were confident they'd get another job with the same pay... read more

Hey, sign up or sign in to add a reaction to my post.
Greptimedb is a timeserie database that embraces cloud-native technology for scalable and reliable application deployment and management. It can be easily deployed and distributed using the Helm chart, and offers robust data storage solutions in the cloud... read more
Hey, sign up or sign in to add a reaction to my post.
The Sysdig Threat Research Team discovered techniques that allowed the AWS WAF to be bypassed using a specialized DOM event. Web Application Firewalls (WAFs) serve as the first line of defense for your web applications, acting as a filter between your application and incoming web traffic to protect .. read more

Hey, sign up or sign in to add a reaction to my post.
Netflix has rebuilt its video processing pipeline to support its streaming service and studio operations, integrating new technologies such as high dynamic range (HDR) and microservice-based computing. This next-generation pipeline allows for rapid innovation, improved system resiliency, and enhance.. read more

Hey, sign up or sign in to add a reaction to my post.
This article explore Podman's features and benefits, comparing it to Docker and describing a step-by-step migration guide.. read more

Hey, sign up or sign in to add a reaction to my post.
Introducing Spiel, a new speech API and framework for desktop Linux and beyond. It aims to leverage existing free desktop technologies and offers simplicity in design for easy adoption... read more
Hey, sign up or sign in to add a reaction to my post.
Kubernetes is a popular container orchestration tool that helps reduce accidental complexity by providing a high-level language to define infrastructure and reduce the need to understand the underlying complexity of running software. However, there is still a significant amount of incidental complex.. read more

Hey, sign up or sign in to add a reaction to my post.
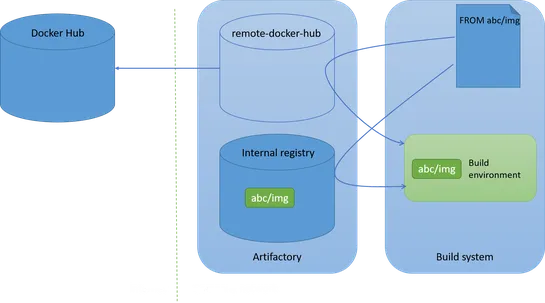
Dependency confusion is a supply chain attack where an attacker can poison the build process by forcing the build system to retrieve a malicious dependency from somewhere on the internet instead of a legitimate internal dependency. This vulnerability can be exploited by an attacker to gain access to.. read more
Hey, sign up or sign in to add a reaction to my post.
Istio 1.19.6 is officially released! You can find the announcementhere... read more
Hey, sign up or sign in to add a reaction to my post.
Some companies use an isolated network or even the complete lack of a network as a security measure to protect from unauthorized access. Working on these systems can be a struggle but it is still possible, and perhaps even more important, to use a proper version control tool like Git. By design Git .. read more
Hey, sign up or sign in to add a reaction to my post.
This tool doesn't have a detailed description yet. If you are the administrator of this tool, please claim this page and edit it.
Hey there! 👋
I created FAUN.dev(), an effortless, straightforward way to stay updated with what's happening in the tech world.
We sift through mountains of blogs, tutorials, news, videos, and tools to bring you only the cream of the crop — so you can kick back and enjoy the best!
