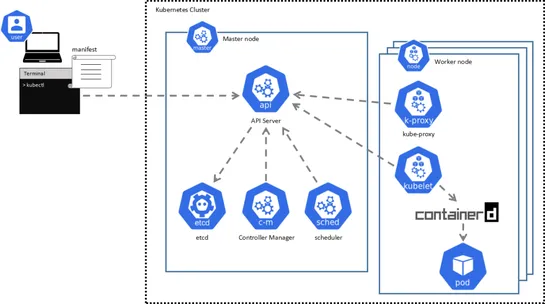
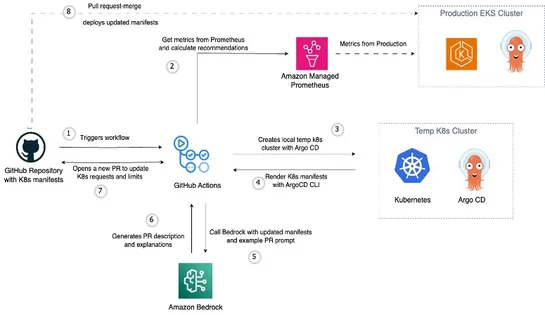
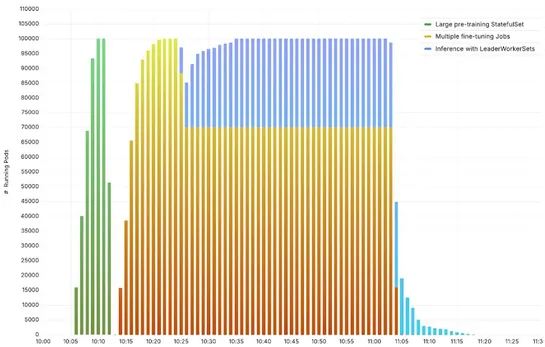
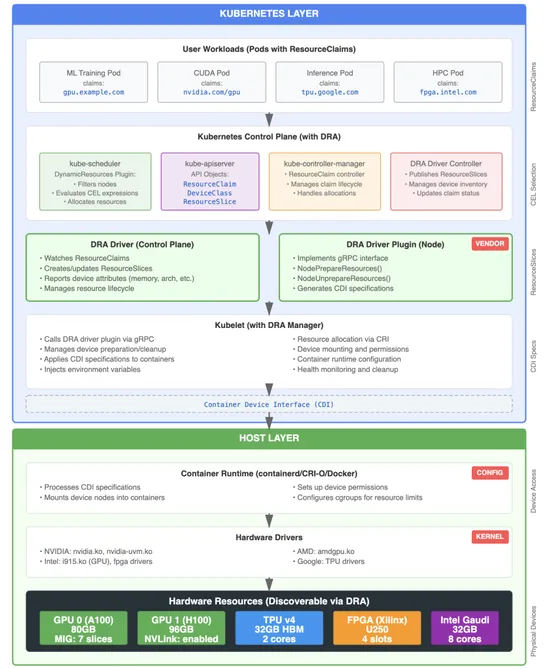
Why "What Happened First?" Is One of the Hardest Questions in Large-Scale Systems
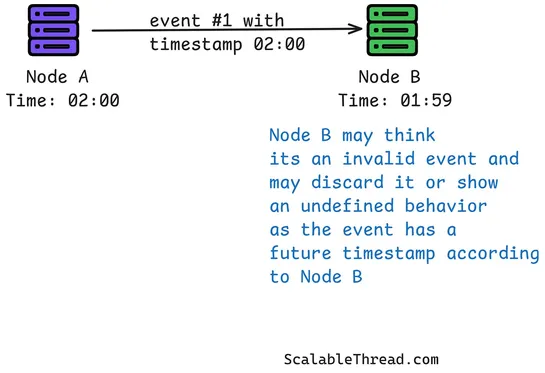
Logical clocks trackevent orderin distributed systems—no need for synced wall clocks. Each node keeps a counter. On every event: tick it. On every message: tack on your counter. When you receive one? Merge and bump. This flips the script. Instead of chasing global time, distributed systems lean int.. read more