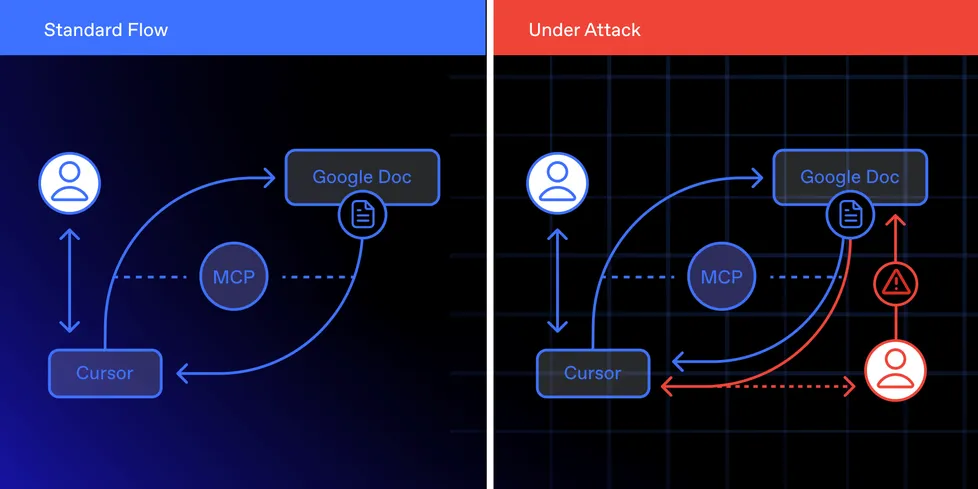
A zero-click exploit is making the rounds—nasty stuff targeting agentic IDEs like Cursor. The trick? Slip a malicious Google Doc into the system. If MCP integration and allow-listed Python execution are on, the document gets auto-pulled, parsed, and runs code. No clicks. No prompts. Just remote code execution, data exfiltration, and vibes ruined.
This isn’t a bug. It’s standard behavior. IDE agents are doing exactly what they’re told—grabbing what looks like a legit asset and running it. That’s the problem.
Give a Pawfive to this post!
Start writing about what excites you in tech — connect with developers, grow your voice, and get rewarded.
Join other developers and claim your FAUN.dev() account now!















