The Hidden AWS Cost Traps No One Warns You About (and How I Avoid Them)
Calling outfive sneaky AWS cost traps—the kind that creep in through overlooked defaults and quiet misconfigs, then blow up your bill while no one's watching... read more
Calling outfive sneaky AWS cost traps—the kind that creep in through overlooked defaults and quiet misconfigs, then blow up your bill while no one's watching... read more

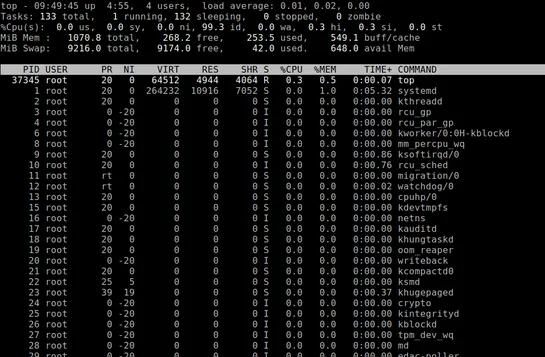
A fresh look at Linux monitoring tools shows the classics still hold—but the visual crowd’s moving in. Old-school command-liners liketopandvmstatremain go-to’s for quick reads. But picks likeNetdata,btop, andMonitbring dashboards, colors, and actual UX. Tools likeiftop,Nmon, andSuricatastretch deep.. read more
Rich Hickey’s classic “Simple Made Easy” talk is making the rounds again—as a mirror held up to dev culture under pressure. The punchline: we keep picking solutions that areeasy but tangled, instead ofsimple and sane. The essay draws a sharp line between that habit and a concept from biology: exapt.. read more
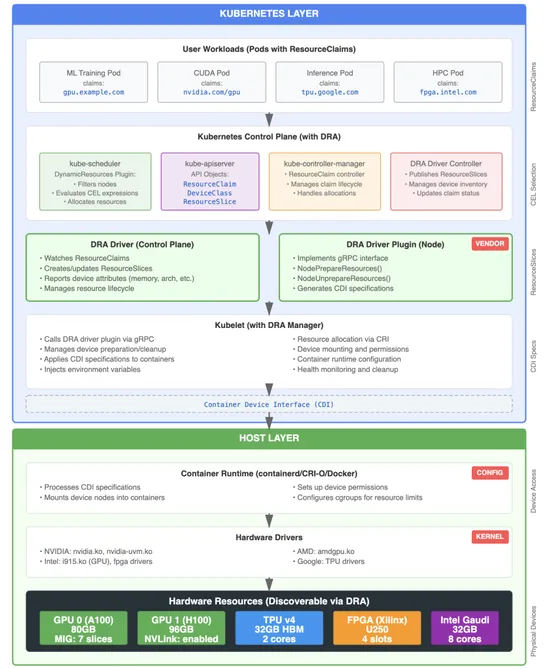
Kubernetes 1.34 brings serious heat for anyone juggling GPUs or accelerators. MeetDynamic Resource Allocation (DRA)—a new way to schedule hardware like you mean it. DRA addsResourceClaims,DeviceClasses, andResourceSlices, slicing device management away from pod specs. It replaces the old device plu.. read more
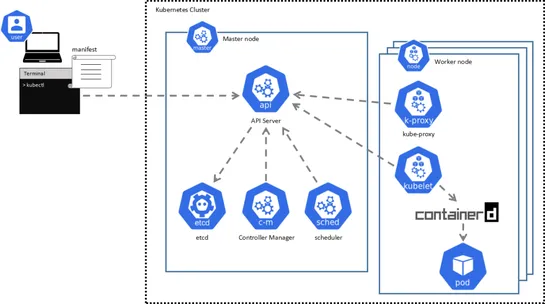
A new attack chain messes withKubernetes DNS resolutionandArgoCD’s certificate injectionto swipe GitHub credentials. With the right permissions, a user inside the cluster can reroute GitOps traffic to a fake internal service, sniff auth headers, and quietly walk off with tokens. What’s broken:GitOp.. read more
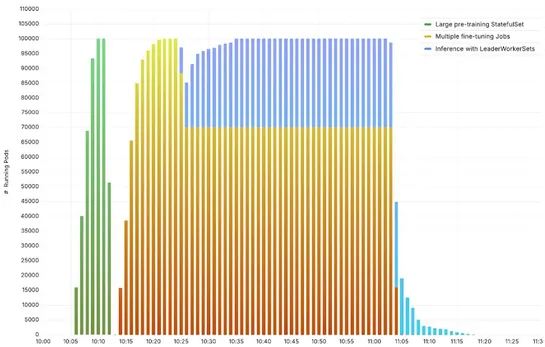
Amazon EKS just cranked its Kubernetes cluster limit to100,000 nodes—a 10x jump. The secret sauce? A reworkedetcdwith an internaljournalsystem andin-memorystorage. Toss in tightAPI server tuningand network tweaks, and the result is wild: 500 pods per second, 900K pods, 10M+ objects, no sweat—even un.. read more
Nigel Douglas discusses the challenges of security in Kubernetes, particularly with traditional base operating systems. Talos Linux offers a different approach with a secure-by-default, API-driven model specifically for Kubernetes. CISOs play a critical role in guiding organizations through the shif.. read more
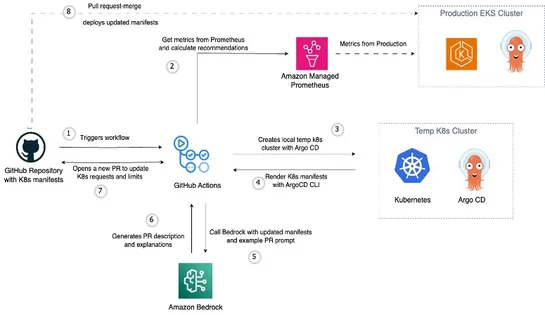
AWS just dropped a GitOps-native pattern for tuning EKS resources—built to runoutsidethe cluster. It’s wired up withAmazon Managed Service for Prometheus,Argo CD, andBedrockto automate resource recommendations straight into Git. Here’s the play: it maps usage metrics to templated manifests, then sp.. read more
AI isn’t just burning compute—it's torching old-school FinOps. Reserved Instances? Idle detection? Cute, but not built for GPU bottlenecks and model-heavy pipelines. What’s actually happening:Infra teams are ditching cost-first playbooks for something smarter—business-aligned orchestrationthat chas.. read more

Older container technologies like Docker have been prone to security vulnerabilities, such as CVE-2019-5736 and CVE-2022-0847, which allowed for potential host system compromise. Podman changes the game by eliminating the need for a persistent background service like the Docker daemon, enhancing sec.. read more