SourceForge Favorite Award 🏆
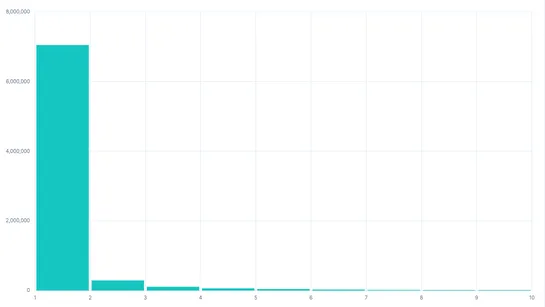
We are proud to share that RELIANOID has been recognized with the SourceForge Favorite Award 🏆 This recognition is granted to only a handful of projects out of more than 500,000 open source projects hosted on SourceForge, based on downloads and user engagement. 👉 With nearly 20 million monthly users..