


Are Kubernetes days numbered?
Google's Kubernetes Engine (GKE) is considered the strongest managed Kubernetes offering, with a focus on reducing engineer involvement in cluster operations. Cloud Run, Google's serverless container offering based on the open-source Knative framework, is becoming an increasingly attractive option w.. read more
The Essential Kubectl Commands: Handy Cheat Sheet
With kubectl, users can create, modify, and delete Kubernetes resources, retrieve logs, and execute commands within pods, making it a versatile and powerful tool for Kubernetes ecosystem. Here's a complete cheat sheet to use kubectl!.. read more
How to Hack Kubernetes (and How to Protect It)
Kubernetes is a valuable resource for container management system development pipelines, but it is susceptible to malicious attacks. To protect the security of a Kubernetes cluster, it is crucial to implement various defense tactics and follow good security practices throughout the container lifecyc.. read more

GKE Security Posture now generally available with enhanced features
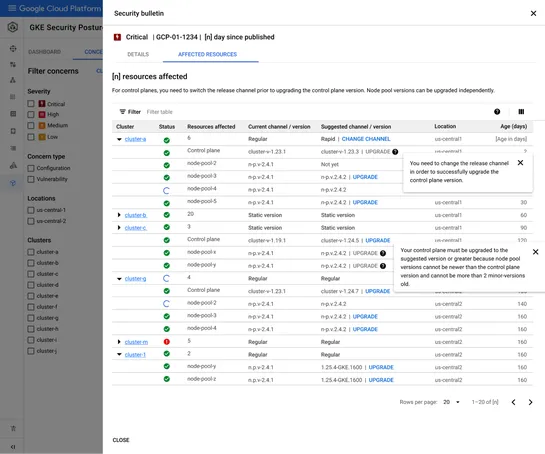
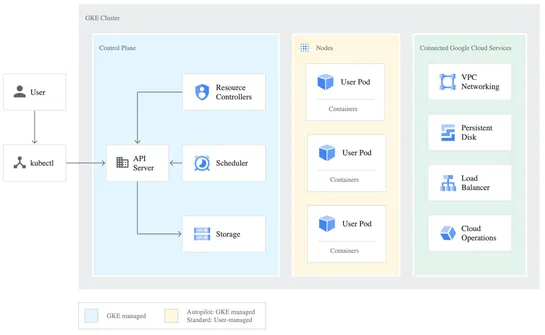
Google Kubernetes Engine (GKE) has announced the availability of its security posture dashboard, which offers a streamlined interface for managing the security of GKE clusters. The dashboard includes features such as misconfiguration detection and vulnerability scanning to ensure the safety and secu.. read more
Analyzing Volatile Memory on a Google Kubernetes Engine Node
Spotify uses containerized workloads on Google Kubernetes Engine (GKE) to run their production workload and detect suspicious behavior. They use an open source alternative method to conduct memory analysis on GKE nodes, combining three open source tools: AVML,dwarf2json, andVolatility 3... read more
Shrink to Secure: Kubernetes and Secure Compact Containers
Reduce your Kubernetes container size to improve security. Smaller containers have benefits such as faster boot time, lower memory usage, and smaller disk footprint. By removing unnecessary software and focusing on essential components, you can reduce vulnerabilities and improve the security of your.. read more





