Post-Quantum Cryptography in Kubernetes
Kubernetes v1.33quietly rides thepost-quantum securitywave, thanks to Go 1.24's hybrid key exchanges. Watch out for version mismatches, though—those could sneakily downgrade your defenses...
Kubernetes v1.33quietly rides thepost-quantum securitywave, thanks to Go 1.24's hybrid key exchanges. Watch out for version mismatches, though—those could sneakily downgrade your defenses...
Cozystackwants local cloud providers to flex by deliveringKubernetes-based managed serviceswithout breaking a sweat. Who needs hyperscalers anyway? Built on open-source goodness, it ditches vendor lock-in, giving these providers the freedom to roll out next-gen infrastructures in style...
GitGuardian's 2024 reportsounds the alarm:23 million secrets slipped through leaks in 2023. A whopping 70% hung around for months. Talk about a security nightmare! EnterHashiCorp VaultandAkeyless. These tools mastered the multi-cloud juggling act and automated secrets management. Result? A satisfyin..

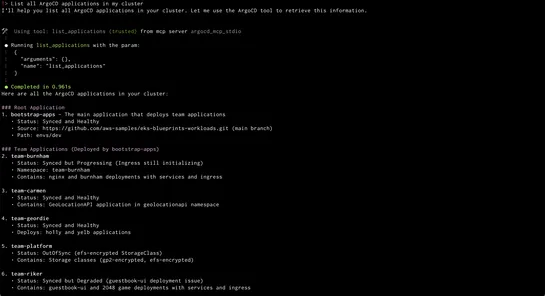
ArgoCD MCP Serverteams up withAmazon Q CLIto shake up Kubernetes with natural language controls. Finally, GitOps that even the non-tech crowd can handle. Kiss those roadblocks goodbye. No more brain strain from Kubernetes. Now, plain language syncs apps, reveals resource trees, and checks health sta..
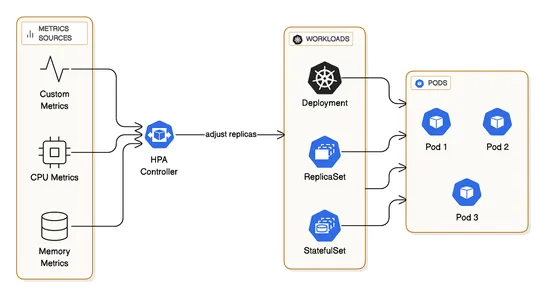
Horizontal Pod Autoscaler(HPA) cranks up pods based on CPU, memory, or custom quirks. A dream for stateless adventures, but you'll need a metrics server.Vertical Pod Autoscaler(VPA) fine-tunes CPU and memory for pods. Works like a charm for jobs where scaling out is sketchy, though it demands restar..
A cyberattack can strike at any time—causing operational disruption, financial loss, and reputational damage. Preparing for and effectively managing a cyber crisis is no longer optional—it's essential. At RELIANOID, we help businesses build robust cyber resilience through advanced solutions and expe..

Instrument NGINX with OpenTelemetry to capture traces, track latency, and connect upstream and downstream services in a single request flow.

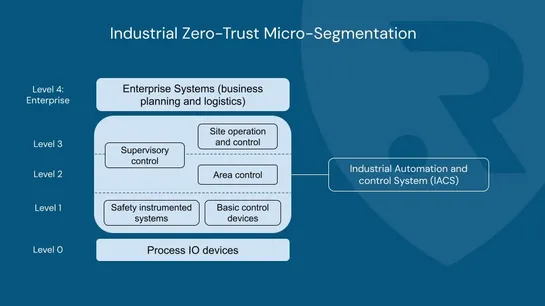
In today's connected industrial world, the convergence of IT & OT brings efficiency—but also new risks. That’s why Zero-Trust Micro-Segmentation is no longer optional. 📌 It divides your network into isolated zones, applies strict access rules, and assumes no user or device is inherently trusted. ✅ K..
Visualize AWS metrics like Lambda, API Gateway, and RDS in Grafana using Last9. No agents, no code, set it up in under 10 minutes.
