
Malware analysis determines if a program/file is malicious. There are two phases in malware analysis.
Obtain malware sample:
There’s a number of online resources you can get malware samples from
- Online courses: Most online courses provide links to the malware files used for demos in the course for the benefit of students who wish to follow the instructor.
- Online repositories: A quick google search will return some results for the popular repos to get samples from, however, I have gotten samples from some of the following:
- https://github.com/Virus-Samples/Malware-Sample-Sources; https://zeltser.com/malware-sample-sources/
Please remember that these are live and dangerous malware!
Do NOT run them unless you are absolutely sure of what you are doing!
They are to be used only for educational purposes only in a controlled and segmented sandbox environment!!!
What is static malware analysis?
Static analysis examines a malware program/file without execution. This provides the safest way to analyse malware without infecting your system. Static analysis extracts information from malware without viewing the code. Metadata such as libraries, file type, resources, and strings can yield clues about the nature of the malware. Hashes — MD5, SHA-1, SHA-256 — can be researched in OSINT to determine if the malware has been previously analysed or identified by antivirus engines. In this post, I’ll share my methodology (alongside popular tools) for static analysis.
Some questions to ask during static analysis:
- Is this file malicious?
- What type of file is this?
- Has anyone already analysed this file?
- What can be identified in the embedded strings?
- Is this file packed or unpacked?
- What can be identified in the PE header of the file?
Methodology & Tools used:
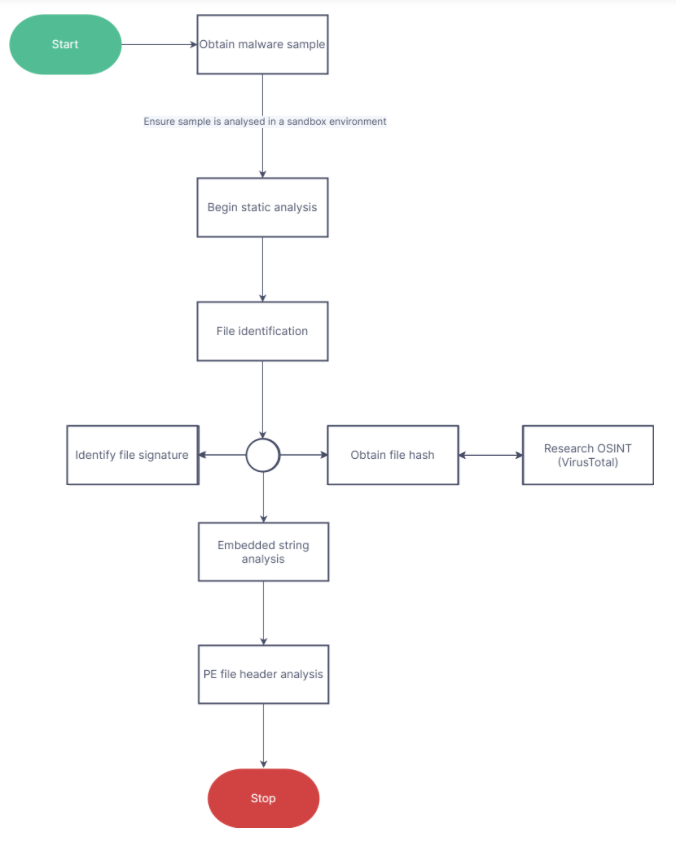
It is important to have a process/methodology in place for static analysis as it involves the following steps that have various other steps which can be missed.
- File identification.
- Embedded string analysis.
- PE file header analysis.
File identification:
This is usually the first step in static analysis. Threat actors usually employ various methods (such as using double extensions) to trick users into executing the malware file, hence it is very important to be able to identify malicious files in the system.
Steps in file identification include:
Determining the file type using file signatures: A file signature in computer programming is a unique identifying number located at the beginning of a file. This number identifies the type of file, giving information about the data contained within the actual file.
- PE files have 4D 5A (MZ) as their first two (2) bytes.
- Read more on file signature: https://www.easytechjunkie.com/what-is-a-file-signature.htm; https://filesignatures.net/index.php?page=all
Some tools for file identification: file command, exeInfoPE, TrID.
Cryptographic hashes: Hashing is a one-way process that takes any file and produces a unique fixed-size output of text called a hash value, or just “hash.” The hash can then be stored and used instead of the file and can be researched in OSINT to determine if the malware has been previously analysed or identified by antivirus engines. The popular hashes are: MD5, SHA-1 & SHA-256. MD5 & SHA-1 hashes have been linked with collisions, i.e. it is possible for two (2) files to have the same hash, to avoid this, I advise using SHA-256 hashes.
Some tools for obtaining file hashes include: certutil, Hashcalc.
Embedded Strings analysis:
Strings are ASCII and Unicode characters embedded within a file. Extracting strings can give clues about the functionality and indicators associated with a malicious file. Filenames, URLs, domain names, IP addresses, registry keys etc can all be identified during embedded strings analysis.
Some tools for string analysis: strings command, BinText
ASCII vs Unicode: https://www.geeksforgeeks.org/ascii-vs-unicode/
PE header analysis:
The Portable Executable (PE) format is a file format for executables, object code, DLLs and others used in 32-bit and 64-bit versions of Windows operating systems. The PE file header consists of a Microsoft MS-DOS stub, the PE signature, the COFF file header, and an optional header.
A popular tool for analysing the PE file header is CFF Explorer.
PE Studio: PeStudio is a tool used for malware analysis, it is the swiss army knife for static analysis.
https://www.varonis.com/blog/pestudio
Flowchart for Static analysis
Start blogging about your favorite technologies, reach more readers and earn rewards!
Join other developers and claim your FAUN account now!
User Popularity
51
Influence
5k
Total Hits
1
Posts














Only registered users can post comments. Please, login or signup.