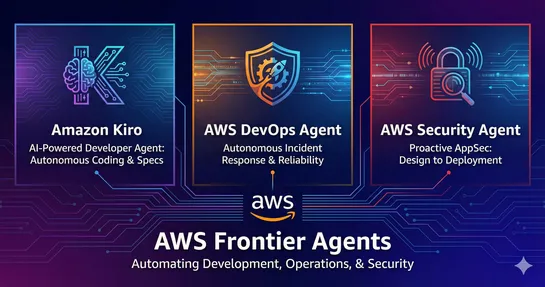
AWS Frontier Agents: Kiro, DevOps Agent, and Security Agent
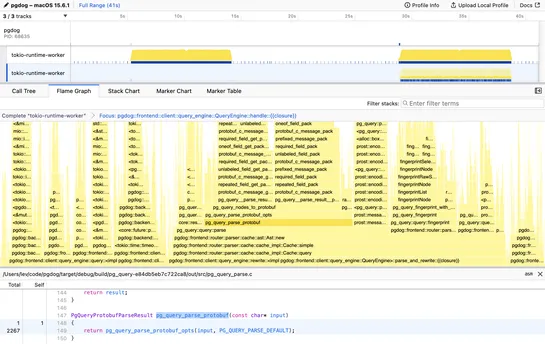
“Frontier Agents” drop straight into incident workflows. They kick off investigations on their own, whether triggered by alarms or a human hand, pulling together logs, metrics, and deployment context fast. Findings show up where they’re needed: Slack threads, tickets, operator dashboards. No shell c.. read more