In this article, we will see the best practices for Docker host security based on 6 scenarios.
Best Practices for Docker Host Security
- Secure and harden your host OS.
- Ensure your host is kept updated.
- Ensure you have the latest version of Docker running.
- Consider the use of a minimal Linux distribution such as Alpine that offers a much smaller threat surface.
- Add your host and containers to a robust vulnerability management plan and constantly scan your host and containers for vulnerabilities.
- Only run the services you need to run.
- Ensure your kernel is up to date.
- Keep up with the latest vulnerability news for the Linux kernel and the Docker platform.
Tutorial prerequisites
- an Ubuntu 18.04 host;
Setup (if you do it locally, just skip this setup)
Install Docker
Update the apt package index and install packages to allow apt to use a repository over HTTPS:
Add Docker’s official GPG key:
Use the following command to set up the stable repository. To add the nightly or test repository, add the word nightly or test (or both) after the word stable in the commands below.
Install Docker Engine
Update the apt package index, and install the latest version of Docker Engine and containerd, or go to the next step to install a specific version:
List the versions available in your repo:
Install a specific version using the version string from the second column, for example,
Verify that Docker Engine is installed correctly by running the hello-world image.
check the status
Scenario based demos
1:Running Docker Containers with an Unprivileged User
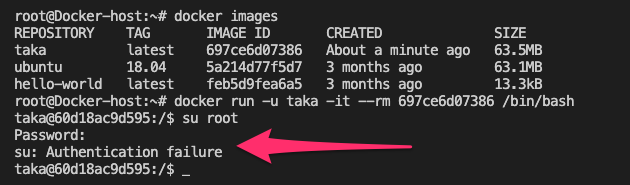
Running Docker containers with an unprivileged user instead of the default “root” user prevents privilege escalation attacks.
As you can see above, it allows a user to run as root.
So countermeasures are
1:reconfigure and build your own Docker images
2:Prior to building your Docker image, specify an unprivileged user in your Dockerfile by adding the following command, replacing <USER> with your username and <GROUP> with a non-sudo group
This is an example of Dockerfile.
Inside
Lets build the secure version of Docker image
You can see the new image listed
We can see that the unprivileged user logged in
You can delete the image
2:Disabling the Docker Container “root” User
You can disable the “root” user by changing the default shell from /bin/bash to /usr/sbin/nologin. This prevents any user on the container from accessing the “root” account irregardless of whether they have the “root” password.
We can see that it fails to become root user. This configuration is only applicable if you want to disable the “root” account completely.
3:Preventing Privilege Escalation Attacks
It is recommended to run your containers with specific permissions and ensure that they cannot escalate their privileges.
4. Limiting Docker Container Kernel Capabilities
it is always recommended to not run containers with the --privileged flag as it overrides any other user permission and security restrictions you have set.
Countermeasures
1:Drop all kernel capabilities
For example, specify a particular kernel capabilities to be used.
5:File System Permissions and Access
The ability to specify file system permissions and access allows you to set up containers with a read only file system or a temporary file system.
1: Run a Docker container with a read-only file system
6:Disabling Inter-Container Communication
It is possible to isolate Docker containers from one another which prevents them from communicating with each other. This can be helpful if you want to isolate a particular Docker container. By default, Docker does not isolate containers, allowing them to communicate with each other.
1: In order to disable inter-container communication, create a new Docker network with the enable_icc option set to false and replacing <NETWORK-NAME> with any desired name.
You can see the details
2:You can now run an isolated container by including the --network flag
Start blogging about your favorite technologies, reach more readers and earn rewards!
Join other developers and claim your FAUN account now!

Takahiro Oda
cloud security engineer
@meibutuoyajiUser Popularity
28
Influence
3k
Total Hits
1
Posts
















Only registered users can post comments. Please, login or signup.